4. Cyber Threats in tourism SMEs
What are cyber threats?
Any circumstance or event with the potential to adversely impact business operations, assets, employees, and/or other organisations, or a nation through a system via unauthorised access, destruction, disclosure, modification of information, and/or denial of service.
There are 3 main types of cyber threats:
- Cybercrime includes single actors or groups targeting systems for financial gain or to cause disruption.
- Cyber-attack often involves politically motivated information gathering.
- Cyberterrorism is intended to undermine electronic systems to cause panic or fear.
What are the main types of cyber threats in tourism SMEs?
When it comes to cyber threat attempts, travel and tourism SMEs are one of the most impacted industries globally.
Cyber-attacks in the travel sector mainly target credit cards, personal identifiable information, hospitality reward programmes and publicly available internet (Walson, 2022).
A PwC Hotel Outlook Report from 2018 to 2022 stated that the hotel industry had the maximum number of data breaches after the retail sector.
According to the WTTC, phishing, malware, and ransomware threats remain constant, with ransomware accounting for 23% of cyber-attacks in 2021, and phishing used in 33% of cyber-attacks. Cyber criminals largely gain access to cyber environments through phishing, credential theft, or remote desktop control (World Travel & Tourism Council and Microsoft, 2022).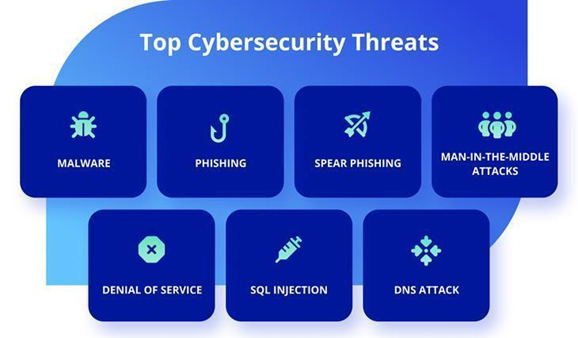
https://motyl-szary.com/2023/03/31/top-cybersecurity-threats-and-proactive-measures-to-protect-personal-and-business-data/
The most common methods used by malicious actors when trying to threaten the cyber security and cyber resilience of a tourism business –
● Malware: this is one of the most common cyber threats which is spread via an unsolicited email attachment or legitimate-looking download. Malware attack compromises an organisation’s sensitive systems and data by infecting them with malicious software such as viruses, worms, Trojan horses, and other spyware (Paraskevas, 2020).
● Phishing: this has always been the most common type of cyber-attack and often occurs through emails. It takes place when cyber criminals send emails to victims which seem to be from a legitimate company (e.g. a bank) and ask for sensitive information (e.g. bank account details, passwords).
● Point-of-sale (POS) attacks: also very common in the travel and tourism sector and gives threat actors valuable data including credit card information such as card numbers and personal identification numbers (PINs).
● Man-in-the-middle: this type of cyber-attack occurs on an unsecure WiFi network where an threat actor could intercept data being passed from the victim’s device and the network.
● Ransomware: the goal of this threat is not to steal data but to deny its owner access to it and make the target pay the attacker directly. Ransomware is programmed to identify the company’s most sensitive or valuable data.
● Botnet attacks: use of large networks, often comprised of numerous computers, smartphones, or intelligent devices (aka. ‘zombie armies’) for carrying out malicious activities such as login attempts, spam attacks, or the takedown of networks, network devices, websites or an organisation’s IT environment.
● Attacks on third-party Service Providers: threat actors also target members of the organisation’s ‘DexteR’ (digital partners and third-party service providers) – these often considered the weaker links in the network and represent attractive aggregation points for sensitive company data (IBM 2018 as cited in Paraskevas, 2020).